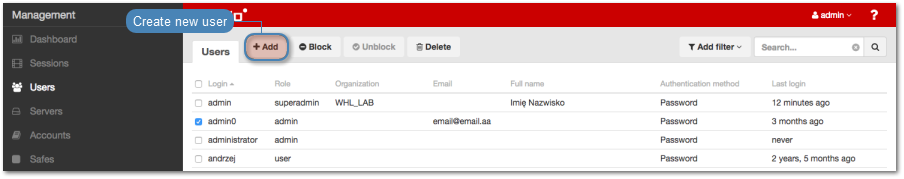
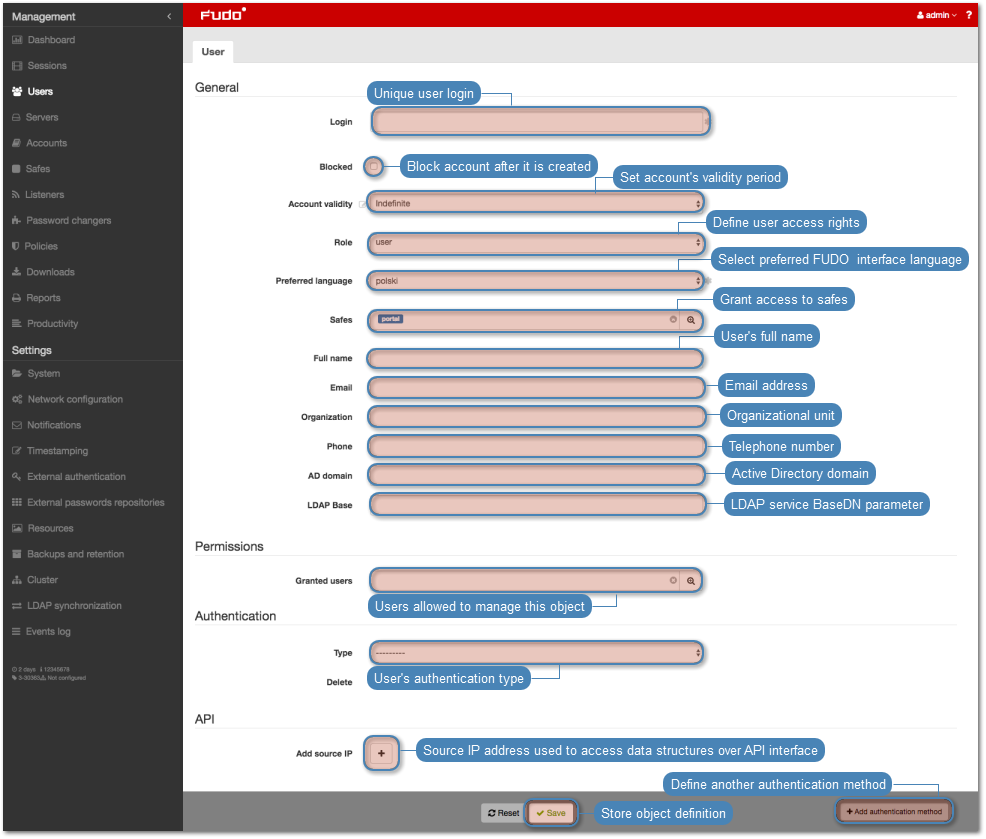
Creating a user¶
Warning
Data model objects: safes, users, servers, accounts and listeners are replicated within the cluster and object instances must not be added on each node. In case the replication mechanism fails to copy objects to other nodes, contact technical support department.
- Select > .
- Click .
Note
Fudo PAM enables creating users based on the existing definitions. Click desired user to access its configuration parameters and click to create a new object based on the selected definition.
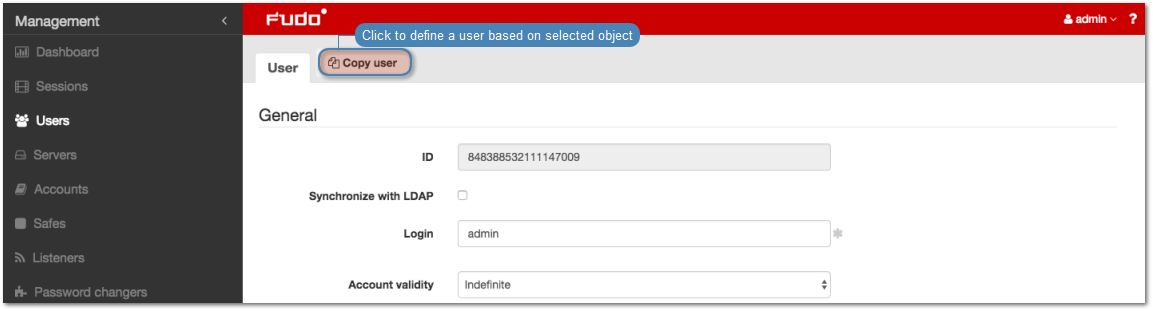
- Enter user login.
Note
- While there can be more than one user with the same username, the login and domain combination must be unique.
- The Login field is not case sensitive.
- Enter Fudo domain.
Note
- With the Fudo domain specified, the user will have to include it when logging into the administration panel or when establishing monitored connections.
- Default domain allows for a discretion - user can either include the domain or leave it out.
- Select the Blocked option to prevent user from accessing servers and resources monitored by Fudo PAM.
- Define account’s validity period.
- Select user’s role, which will determine the access rights.
Note
Access rights restrictions also apply to API interface access.
| Role | Access rights |
|---|---|
| user |
|
| service | Accessing SNMP information. |
| operator |
|
| admin |
|
| superadmin |
|
- Select user’s preferred language in Fudo PAM administration panel.
- Grant access to safes.
Note
Drag and drop safe objects to change the order in safes are processed upon establishing connection.
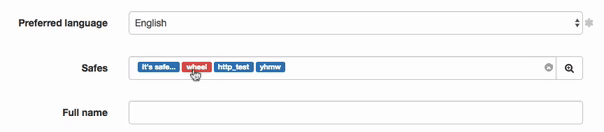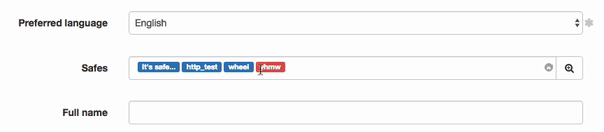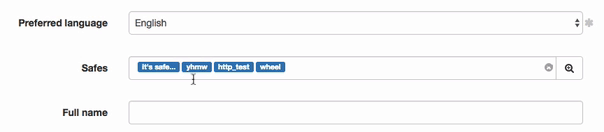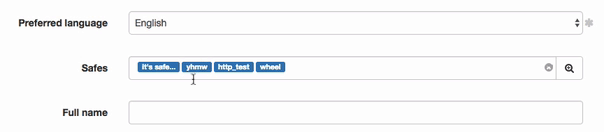
SSH_safe implies that the Reveal password option is disabled.
RDP_safe implies, that the Reveal password option is enabled.
Click safe to define time access policy.
- Enter user’s full name.
- Enter user’s email address.
- Enter user’s organizational unit.
- Enter user’s phone number.
- Provide user’s Active Directory domain.
Note
If there are two users with the same login, one of which has the domain configured the same as the default domain, and the other does not have the domain defined, Fudo PAM will report authentication problem as it cannot determine which user is trying to connect.
- Enter LDAP service BaseDN parameter.
Note
- LDAP base is necessary for authenticating the user using the Active Directory service.
- E.g. for
example.comdomain, the LDAP base parameter value should bedc=example,dc=com.
- In the Permissions section, select users allowed to manage this user object and in case of operators/administrators, assign management privileges to selected data model objects.
Note
Granting a user access to certain session requires assigning management priviliges to: server, account, user and safe objects that were used in the given connection.
- In the Authentication section, select the Authentication failures option to block the user automatically after exceeding the number of failed login attempts.
Note
The authentication failures counter is enabled only if the Authentication failures option is set in > in the User authentication and sessions section.
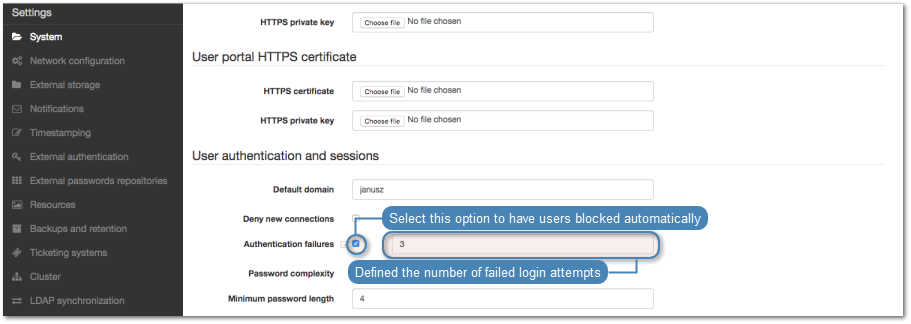
- Select the Enforce static password complexity option to force static passwords to conform to specified settings.
Note
Password complexity is defined in > in the Users authentication and sessions section.
- Select authentication type.
External authentication
- Select
External authenticationfrom the Type drop-down list. - Select external authentication source from the External authentication source drop-down list.
Note
Refer to External authentication topic for more information on external authentication sources.
Password
- Select
Passwordfrom the Type drop-down list. - Type password in the Password field.
- Repeat password in the Repeat password field.
- Select Required password change on next login to have the user change the password on next login attempt.
Note
If you select the Required password change on next login option, the user will not be able to access servers directly (bypassing the User Portal) using native protocols clients. The user will have to change the password using the User portal.
SSH key
- Select
SSH keyfrom the Type drop-down list.
- Click i icon and browse the file system to find the public SSH key used for verifying user’s identity.
One-time password
Warning
One-time passwords are used for implementing AAPM use case scenarios.
- Select
One-time passwordfrom the Type drop-down list.
- Click to define more authentication methods.
Note
When processing user authentication requests, Fudo PAM verifies login credentials against defined authentication methods in order in which those methods have been defined.
- In the API section, click i and define IP address used by an external system to communicate with Fudo over API.
- Click .
Related topics: