Deployment scenarios¶
Note
It is advised to design network topology, so FUDO only mediates administrative connections. It will allow lowering system load, network traffic optimization as well as maintaining access to hosted services in case of hardware malfunction.
Bridge
In bridge mode FUDO mediates communication between users and servers regardless whether the traffic is being monitored (i.e. it uses any of supported protocols) or not.

When mediating the traffic, FUDO preserves source IP address when forwarding requests to destination servers.
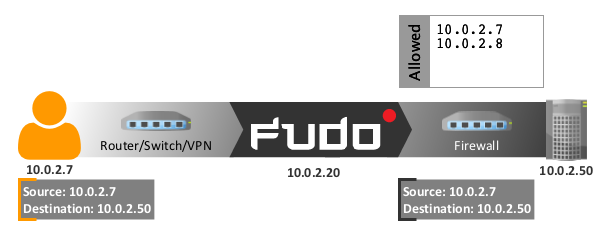
Such solution allows keeping existing rules on firewalls which control access to internal resources.
For more information on configuring bridge refer to the Network configuration topic.
Forced routing
Forced routing mode requires using a properly configured router. Such solution allows controlling network traffic in third ISO/OSI network layer, so only administrative requests are routed through FUDO and the rest of the traffic is forwarded directly to the destination server.
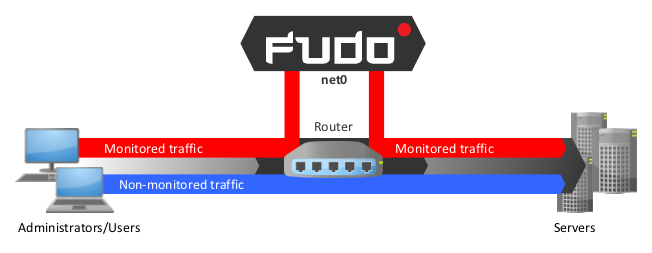
This mode does not require changes in existing network topology and enables network traffic optimization due to separating requests from system administrators and regular users.
Connection modes
Transparent
In transparent mode, users connect to destination server using given server’s IP address.

Gateway
In gateway mode, users connect to destination server using the server’s actual IP address. FUDO mediates connection with the server using own IP address. This ensures that the traffic from the server to the user goes through FUDO.
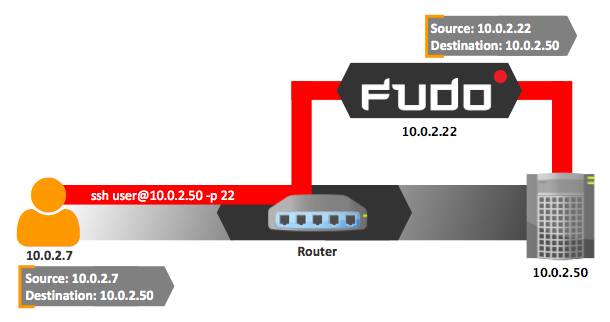
Proxy
In proxy mode, administrator connects to destination server using combination of FUDO IP address and unique port number assigned to given server. Uniqueness of this combination enables establishing connection with a particular resource.
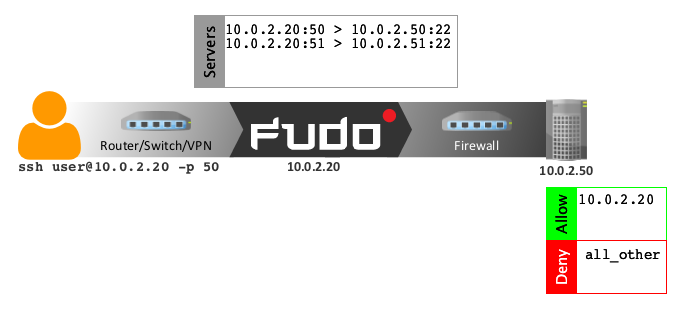
Such approach enables concealing actual IP addressing and allows configuring servers to only accept requests sent from FUDO.
Bastion
In bastion mode, target host is specified within the string identifying the user, e.g. ssh john_smith#mail_server@10.0.0.8.

Related topics: