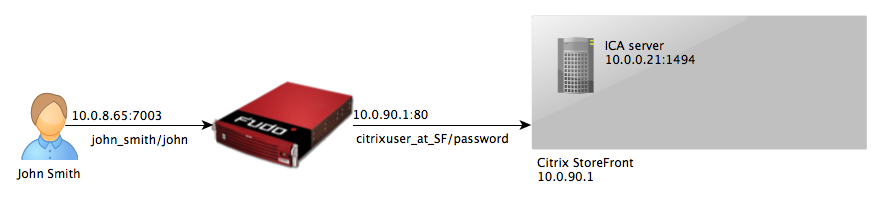
ICA via Citrix StoreFront¶
This chapter contains an example of a basic Wheel Fudo PAM configuration, to monitor access to a remote server over ICA protocol with the connection itself being initiated via the Citrix StoreFront.
Prerequisites¶
The following description assumes that the system has been already initiated. For more information on the initiation procedure refer to the System initiation topic.
Configuration¶

Adding an ICA server
is a definition of the IT infrastructure resource, which can be accessed over one of the specified protocols.
- Select > .
- Click .
- Provide essential configuration parameters:
| Parameter | Value |
|---|---|
| General | |
| Name | ica_server |
| Blocked |  |
| Protocol | ICA |
| Description |  |
| Permissions | |
| Granted users |  |
| Destination host | |
| Address | 10.0.0.21 |
| Port | 1494 |
| Use TLS |  |
- Click .
Adding an ICA listener
determines server connection mode (proxy, gateway, transparent, bastion) as well as its specifics.
- Select > .
- Click .
- Provide essential configuration parameters:
| Parameter | Value |
|---|---|
| General | |
| Name | ica_listener |
| Blocked |  |
| Protocol | ICA |
| Permissions | |
| Granted users |  |
| Connection | |
| Mode | proxy |
| Local address | 10.0.150.151 |
| Port | 2494 |
| Use TLS |  |
- Click .
Adding an account for the ICA server
defines the privileged account existing on the monitored server. It specifies the actual login credentials, user authentication mode: anonymous (without user authentication), regular (with login credentials substitution) or forward (with login and password forwarding); password changing policy as well as the password changer itself.
- Select > .
- Click .
- Provide essential configuration parameters:
| Parameter | Value |
|---|---|
| General | |
| Name | ICA_forward |
| Blocked |  |
| Type | forward |
| Session recording | all |
| OCR sessions |  |
| Delete session data after | 61 days |
| Permissions | |
| Granted users |  |
| Server | |
| Server | ica_server |
| Credentials | |
| Replace secret with |  |
| Forward domain |  |
- Click .
Adding a Citrix StoreFront server
is a definition of the IT infrastructure resource, which can be accessed over one of the specified protocols.
- Select > .
- Click .
- Provide essential configuration parameters:
| Parameter | Value |
|---|---|
| General | |
| Name | citrix_storefront |
| Blocked |  |
| Protocol | Citrix StoreFront (HTTP) |
| HTTP timeout | 900 |
| Description |  |
| Permissions | |
| Granted users |  |
| Destination host | |
| Address | 10.0.90.1 |
| Port | 80 |
| Bind address | Any |
| URL | http://10.0.90.1/Citrix/StoreWeb/ |
- Click .
Adding a Citrix StoreFront listener
determines server connection mode (proxy, gateway, transparent, bastion) as well as its specifics.
- Select > .
- Click .
- Provide essential configuration parameters:
| Parameter | Value |
|---|---|
| General | |
| Name | citrix_storefront_listener |
| Blocked |  |
| Protocol | Citrix StoreFront (HTTP) |
| Permissions | |
| Granted users |  |
| Connection | |
| Mode | proxy |
| Local address | 10.0.8.65 |
| Port | 7003 |
| Use TLS |  |
- Click .
Adding an account for the Citrix StoreFront server
defines the privileged account existing on the monitored server. It specifies the actual login credentials, user authentication mode: anonymous (without user authentication), regular (with login credentials substitution) or forward (with login and password forwarding); password changing policy as well as the password changer itself.
- Select > .
- Click .
- Provide essential configuration parameters:
| Parameter | Value |
|---|---|
| General | |
| Name | citrixuser_at_SF |
| Blocked |  |
| Type | regular |
| Session recording | all |
| OCR sessions |  |
| Delete session data after | 61 days |
| Permissions | |
| Granted users |  |
| Server | |
| Server | citrix_storefront |
| Credentials | |
| Domain | tech.whl |
| Login | citrixuser |
| Replace secret with | password |
| Password | password |
| Repeat password | password |
| Password change policy | Static, without restrictions |
| Password changer | |
| Password changer | none |
| Privileged user |  |
| Privileged user password |  |
Adding a user
User defines a subject entitled to connect to servers within monitored IT infrastructure. Detailed object definition (i.e. unique login, full name, email address etc.) enables precise accountability of user actions when login and password are substituted with a shared account login credentials.
- Select > .
- Click .
- Provide essential user information:
| Parameter | Value |
|---|---|
| Login | john_smith |
| Blocked |  |
| Account validity | Indefinite |
| Role | user |
| Preferred language | English |
| Full name | John Smith |
john@smith.com |
|
| Organization |  |
| Phone |  |
| AD Domain |  |
| LDAP Base |  |
| Permissions | |
| Granted users |  |
| Connections | |
| Connections |  |
| Authentication | |
| Type | Password |
| Password | john |
| Repeat password | john |
- Click .
Defining a safe
directly regulates user access to monitored servers. It specifies available protocols’ features, policies and other details concerning users and servers relations.
- Select > .
- Click .
- Provide essential configuration parameters:
| Parameter | Value |
|---|---|
| General | |
| Name | ica_safe |
| Blocked |  |
| Login reason |  |
| Notifications |  |
| Policies |  |
| Users | john_smith |
| Protocol functionality | |
| RDP |  |
| SSH |  |
| VNC |  |
| Accounts | |
citrixuser_at_SF |
citrix_storefront_listener |
ICA_forward |
ica_listener |
- Click .
Connecting to remote resource¶
- Navigate your web browser to the
10.0.8.65:7003web address. - Enter user login and password to log in into the Citrix StoreFront interface.
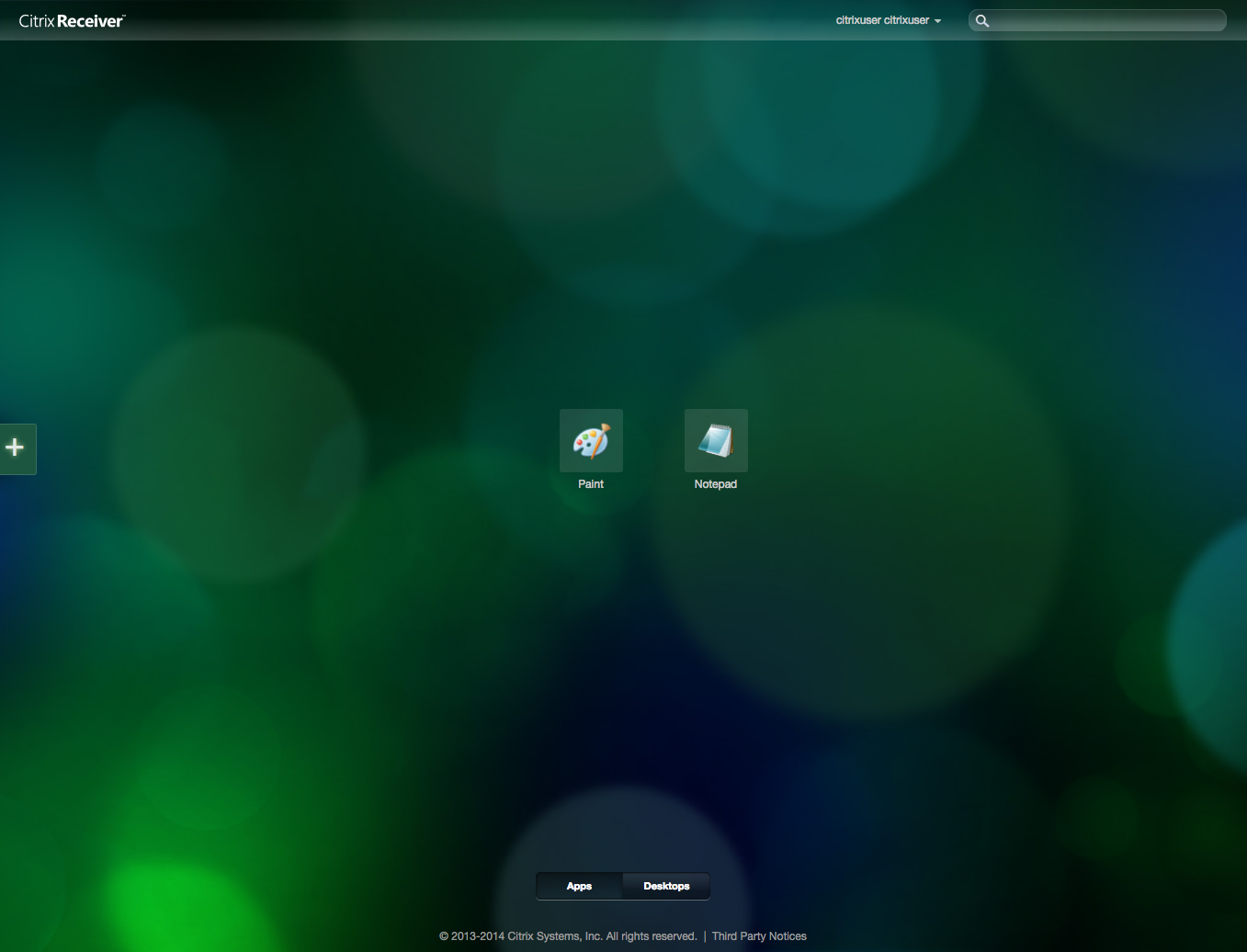
- Click desired element to establish ICA connection with selected resource.
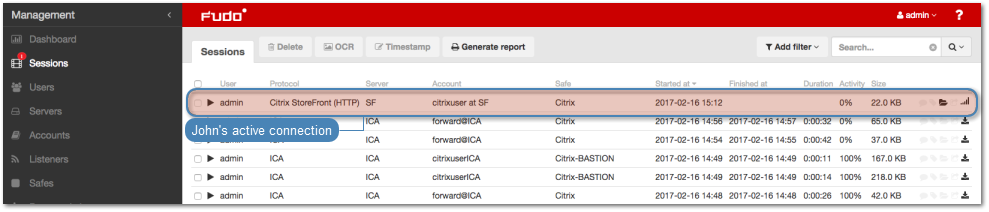
Viewing user session¶
- Open a web browser and go to the Wheel Fudo PAM administration page.
- Enter user login and password to log in to Wheel Fudo PAM administration panel.
- Select > .
- Find John Smith’s session and click i.
Related topics: